When you're processing hundreds of applications per role, spotting the fraudulent ones feels like finding needles in a haystack. Except the needles are getting better at looking like hay, and some of the hay might actually be needles in disguise.
We spoke with Talent Acquisition leaders from SentinelOne, NiCE, and our product team building Gem's fraud detection tools to understand how and where to spot fraudulent candidates throughout the hiring funnel. The goal isn't to eliminate every possibility of fraud at any cost. It's to implement targeted defenses at each stage that match the actual risk you're facing.
In our previous blogs, we outlined the five types of fraud and how to train recruiters to spot fraudsters. In this one, we'll dive into practical techniques for stopping it at each stage of your hiring funnel.
Top of funnel: Application and screening
Fraud at the application stage often involves automated bots, AI-generated resumes, or stolen identities submitting applications at scale. The goal here is to filter out obvious fraud without adding friction for real candidates.
Behavioral pattern detection
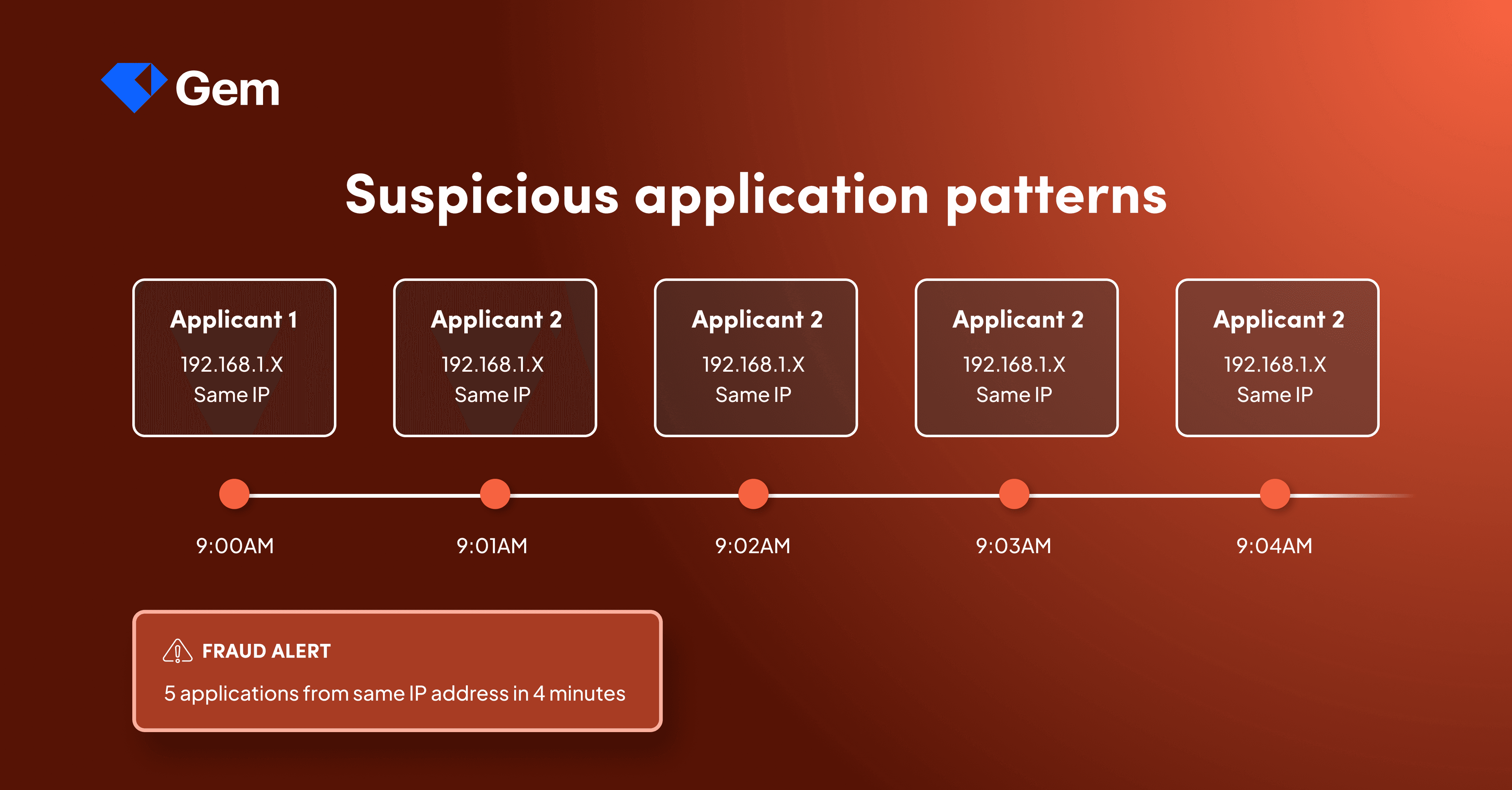
Beyond automated tools, watch for red flags in application patterns. Multiple applications from the same IP address within minutes, identical resume formatting across supposedly different candidates, or application timestamps that suggest inhuman speed all signal potential fraud.
“[State-sponsored fraudsters] are using deep fakes to generate fake images that look like real people. They have people in the Midwest that they're paying to create these laptop farms where they route their interviews through there, so it looks like the IP is coming from a location in the US. The attacks by these state-sponsored actors are getting quite sophisticated and that's where I think it's going to be an arms race.” - Steve Bartel, CEO at Gem
Resume forensics
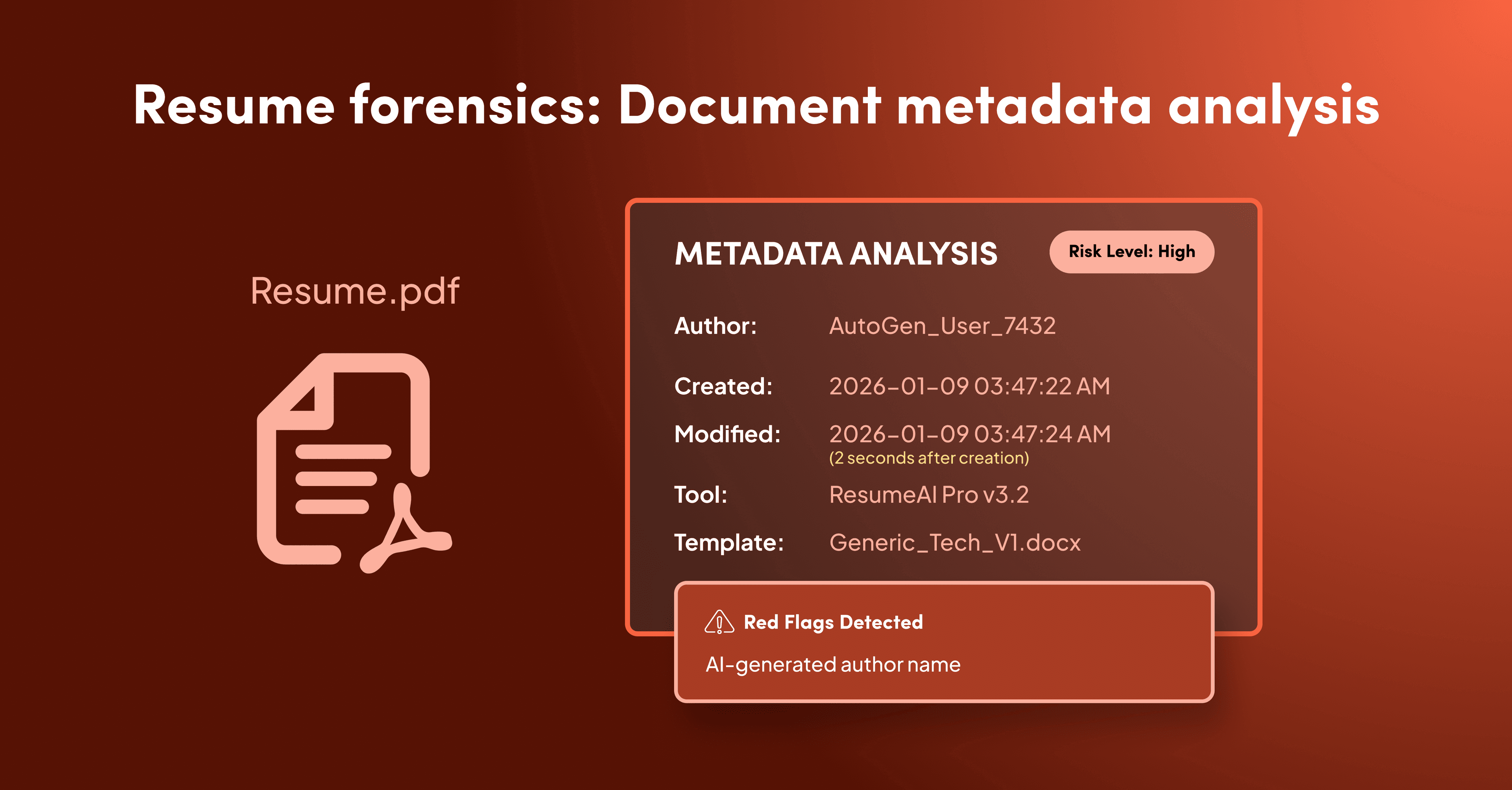
Every digital document carries metadata — a "digital fingerprint" that reveals when it was created, who authored it, and what tools were used. Inspect document metadata for signs that multiple "different" candidates submitted resumes created by the same author or generated by AI tools with identical formatting signatures.
Profile cross-verification
Compare resume details against LinkedIn profiles and public records. Recently created profiles with minimal connections, employment date mismatches, or biographical inconsistencies warrant deeper investigation. This verification should happen during initial screening, not after you've invested time in interviews.
Honeypot fields
Add invisible form fields to your application that only bots can detect and fill out. When these fields contain data, you know the submission came from an automated system rather than a human candidate. This simple technique catches bot-driven fraud before it enters your pipeline.
AI-powered fraud detection
These tactics work best when bundled together in a technology solution that can scan applications at scale. Gem's Fraud Detection Agent uses AI to identify fraud patterns across millions of applications, automatically flagging suspicious activity before it reaches your recruiters.
The agent scans for multiple fraud indicators — email addresses that follow suspicious patterns, applications exhibiting bot-like behavior, coordinated fraud campaigns where multiple fake candidates apply simultaneously, and the behavioral patterns mentioned above. It assigns risk scores to applications and surfaces the most concerning cases for human review, without adding extra steps to your application process or creating friction for legitimate candidates.

Mid-funnel: Interviews and assessments
This stage faces increasingly sophisticated fraud: proxy interviews where someone else poses as the candidate, and real-time AI assistance that feeds answers during technical assessments. Your defenses need to validate identity and capabilities.
Video identity verification
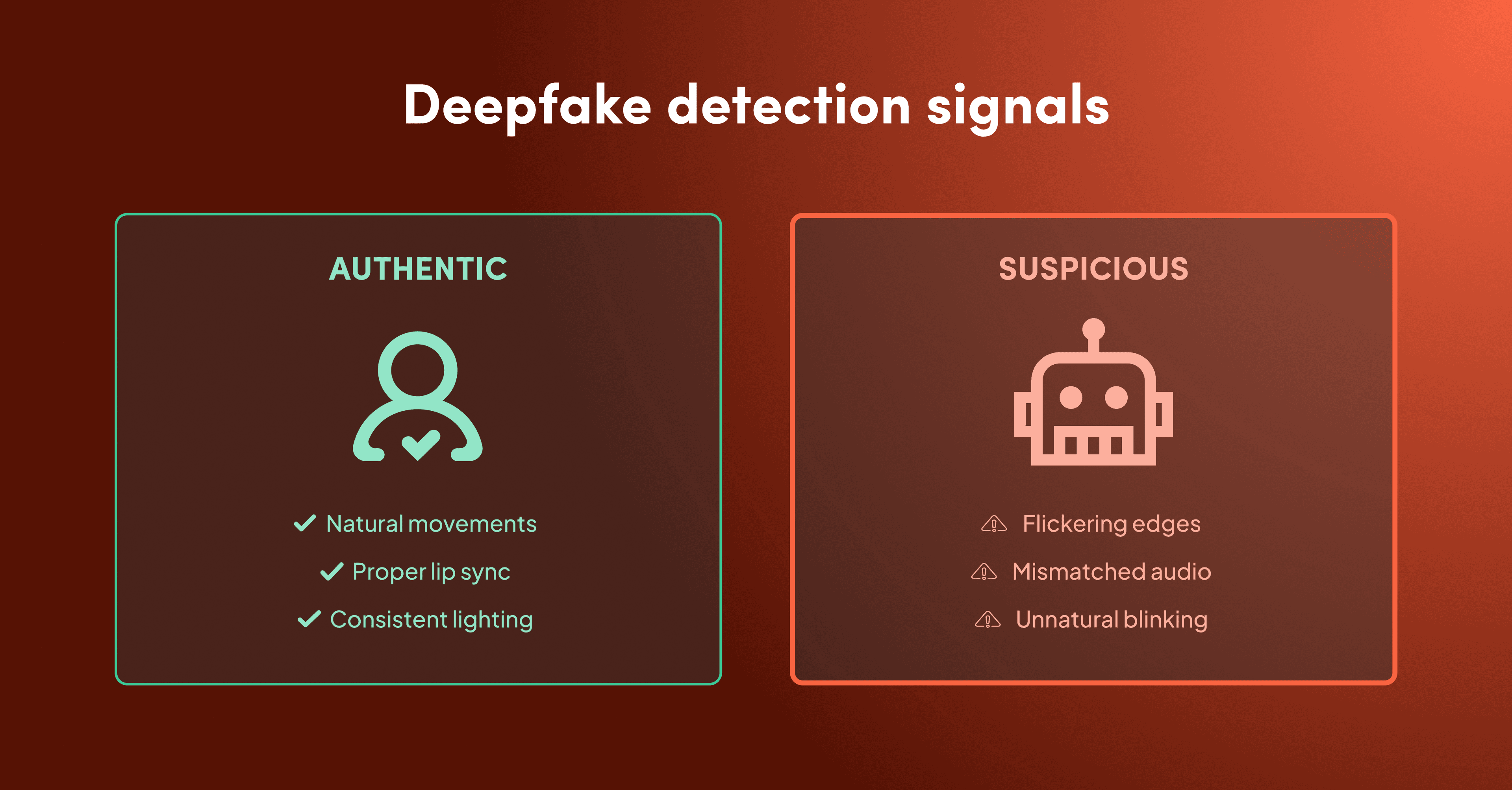
Require cameras on for all video interviews. Watch for deepfake signals, such as unnatural facial movements, flickering around the face edges, or poor lip-syncing. While deepfake technology is advancing, most fraud attempts still use simpler methods that these checks can catch.
"A lot of these fraudulent candidates do actually have the technical expertise. They're just not who they say they are or where they say they are, which makes it more difficult to try to sort that out." - Rebecca Boersma, Senior Director of Recruiting at SentinelOne
The no-earphones approach
Ask candidates to remove headphones during interviews. This prevents off-camera coaching or real-time audio feeds from AI assistants. While it may feel awkward to request, frame it as standard interview protocol.
Structured probing questions
Break the flow of rehearsed answers with unscripted follow-up questions. Dive deeper into specific resume claims with technical minutiae. Real candidates can improvise. Fraudsters and AI assistants struggle with unexpected pivots.
Bottom of funnel: Verification and offer
Final-stage verification ensures that the person accepting your offer is the same person who will be present on day one. This is your last line of defense before onboarding costs accumulate.
Multi-stage identity proofing
Use verification services to validate government-issued IDs and biometric liveness checks (live selfies, not static photos). Conduct this verification twice: once during the interview process and again upon acceptance of the offer. Fraudsters can maintain the facade through interviews, but disappear when concrete verification is required.
Reference audits
Conduct phone references rather than accepting email-only verifications. Use background check services to verify that references are real individuals with verifiable connections to the candidate, rather than fictitious contacts created to support a fraudulent scheme.
Payment and banking
Review where new hires request direct deposits to be sent. Bank accounts in geographic locations unrelated to their stated residence can indicate fraud, particularly in schemes where overseas fraudsters pose as US-based candidates.
Post-hire: Onboarding verification
Your fraud prevention strategy shouldn't end when the offer is accepted. The first days of employment provide critical opportunities to confirm who you thought you hired.
Day one verification
Conduct a brief live video call or in-person meeting on the first day to confirm the person starting the job matches who you interviewed. For remote roles, this could be a casual "welcome aboard" video chat with their manager. For higher-risk roles or when previous fraud indicators were present, consider requiring an on-site onboarding process where new hires complete first-day paperwork and orientation in person, providing an additional layer of identity verification.
Equipment and access monitoring
For remote employees, note if unusual software (particularly remote access tools) gets installed immediately after equipment delivery. This can indicate someone other than the employee is accessing company systems.
Candidate fraud prevention with Gem and Tofu
Gem's Fraud Detection Agent powered by Tofu catches fraud at the application stage, preventing fraudulent candidates from consuming interview time. The agent automatically evaluates applications using multiple fraud signals and assigns a clear risk level — with zero added friction for recruiters or candidates.
We're not the only fraud detection solution on the market, but we've taken a different approach — one that prioritizes both effectiveness and user experience.
Smarter detection and risk evaluation: Most solutions just flag suspicious signals and leave you to figure out what they mean. Gem provides complete risk assessments with clear levels (high, medium, low) and 90%+ accuracy.
Zero friction for recruiters and candidates: Other solutions require candidates to upload IDs and take selfies for biometric verification, which can be a cumbersome process. Gem's fraud detection runs automatically in the background — no additional steps for candidates, no new tools for recruiters.
Flexible pricing: We charge per application with per-job controls. You decide which roles need fraud detection based on risk and volume. We're building toward application-level control within jobs for even greater flexibility. We'll share detailed pricing when we open early access next month.
The balanced approach to fraud prevention
By combining automated detection tools like Gem with targeted human verification at critical stages, you can maintain hiring efficiency while protecting your organization from fraudulent candidates.
Ready to protect your hiring process from fraud? Learn how Gem's Fraud Detection Agent automatically identifies suspicious applications before they waste your team's time or create security risks. Join the waitlist to be among the first companies with access.
Share
Your resource for all-things recruiting
Looking for the latest data, insights, and best practices? Welcome to the Gem blog. We've got you covered.